What is ransomware?
Ransomware is a type of malware that encrypts sensitive data and files and causes the owners to lose access to them. This attack can infect a single device, but also spread across the entire network to encrypt an even larger volume of data.
The peculiarity of ransomware is that cybercriminals attack computers and other devices and demand payment of a “ransom” to regain access to that data, usually by means of bitcoins and other cryptocurrencies, in transactions that cannot be traced.
“Ware” is used in words like malware and spyware to denote malicious programs. With this, we conclude that “ransomware” is malicious software that demands users to pay a reward to recover encrypted files.

Unfortunately, data available on the Statista portal show that the number of ransomware attacks worldwide per year is quite large:
- 2014: 3.2 million
- 2015: 3.8 million
- 2016: 638 million
- 2017: 184 million
- 2018: 204.24 million
- 2019: 187.9 million
- 2020: 304 million
However, here is an important piece of information: the FBI does not indicate paying the ransom in ransomware cases. This does not guarantee that access to the data will actually be restored, and it also encourages criminals to look for more victims and encourages others to engage in this illegal practice.
Therefore, the ideal is to seek the help of experts to help you, such as Bot, which has more than a decade of experience in the data recovery segment and can propose the most suitable solution to recover ransomware.
What is the purpose of ransomware?
Just as in kidnapping, the goal of ransomware is to get the victims to become the criminals’ hostages. This has great psychological weight, and there is no certainty that access to the data will be restored.
The value that sensitive data carries is very high. After all, they may have sensitive information about a company’s customers, bank details, financial spreadsheets, and a host of other possibilities, which puts the victims in a totally unfavorable position.
The scare of encountering a ransomware attack, in addition to this emotional charge, is what can increase the chances that victims will pay what was requested. However, this transaction cannot be traced, so it makes it difficult to find out who is behind this activity.
Usually, cybercriminals are not so interested in the data, they just prevent people and companies from accessing it in order to eventually get the ransom value.
How did ransomware come about?
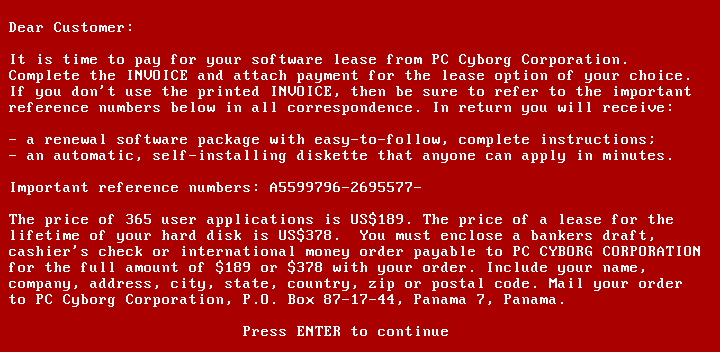
The first ransomware attack on record was the “AIDS Trojan”, malware written by evolutionary biologist Dr. Joseph Popp in the year 1989. It was sent on approximately 20,000 diskettes, named the “AIDS Information Introductory Diskette”, to the participants of a WHO conference on AIDS.
Also called Aids Info Disk or PC Cyborg Trojan, it replaces the PC file “AUTOEXEC.BAT”. The malware then started counting the number of times the computer was booted, and after 90 boots, it hid directories and encrypted the names of all files on the “C:” drive, rendering the system unusable.
The message that appeared on the computer screen after the 90th boot was as follows:
Source:https://upload.wikimedia.org/wikipedia/commons/e/ec/AIDS_DOS_Trojan.png
For 365 boots from his own hard drive, the victim would have to pay a fee of $189, while a “lifetime license” cost $378. Out of curiosity: considering January 1989, these amounts would have the same purchasing power of US$ 410.48 and US$ 820.97 in February 2021, respectively.
The concept of ransomware has developed over time and has become even more lethal with the mass use of the Internet, and has made it harder for criminals to track with the advent of cryptocurrencies.
How does ransomware infection work?
The process can be divided into three steps. The concept of ransomware file encryption was invented and implemented by Adam L. Young and Moti Yung at Columbia University and presented at the IEEE Security and Privacy Symposium in 1996.
Called crypto-viral extortion, the concept was inspired by the second stage of Alien, called the “Facehugger” in the 1979 movie of the same name, and consists of the following protocol between the criminal and the victim:
- [criminal → victim] The criminal generates a key pair and puts the public key into his malware, which is released.
- [victim→ criminal] To proceed with cryptoviral extortion, the malware generates a random symmetric key and encrypts the victim’s data with it. The malware’s public key encrypts the symmetric key, which is called hybrid encryption, and results in an asymmetric ciphertext as well as a symmetric ciphertext with the victim’s data. The symmetric key and the original text are zeroed out to prevent recovery, and the victim then sees a message that includes the asymmetric ciphertext and how he or she should proceed to pay the ransom. The victim then sends the asymmetric cipher text and the money to the criminal.
- [criminal→ victim] The criminal receives the payment, decrypts the asymmetric ciphertext with his private key, and then sends the symmetric key to the victim, who decrypts the encrypted data with this key. Then the attack is finalized.
This complexity shows how data hijacking by ransomware attack is something very well elaborated. But with Bot’s help, you will get all the help you need to regain access to your data in the most secure and cost-effective way possible.
What are the most common methods for distributing ransomware?
A great answer to this question can be seen from data available from the Statista portal, which shows the top cybersecurity methods and vulnerabilities causing ransomware infections. Check it out:
- Phishing or spam e-mails: 54%.
- User malpractice or naivety: 27
- Lack of cyber security training: 26
- Weak passwords or access control failures: 21%.
- Open access to RDPs (Remote Desktop Protocol): 20%.
- Clickbaits: 17%.
- Malicious sites or internet advertisements: 14%.
- Lost or stolen user credentials: 10%.
- Lack of funding for IT security solutions: 8%.
- Lack of executive buy-in for adopting security solutions: 8%.
What are the types of ransomware?
Basically, there are two types of ransomware:
Crypto ransomware
Also known as “Data Locker,” this ransomware encrypts the files stored on a computer or mobile device with the goal of extorting the victim for money. Encryption “scrambles” the contents of the files, so that they become unreadable.
Crypto ransomware looks for flaws and weaknesses in computers and devices in search of data that has not been backed up. This is a very cunning type of malware, as it encrypts all valuable data before it is revealed to the victim.
Generally, it does not block the whole computer or device. Therefore, victims can still access any area that is not encrypted.
Locker ransomware
Locker ransomware, in turn, locks and shuts down the entire computer or mobile device. Victims are asked to pay a ransom to release access.
Generally, the locked system only allows the victim limited access. Some parts of the keyboard may get stuck or the mouse may stop working, which prompts the person to answer what the criminal wants.
Locker ransomware does not usually infiltrate the entire computer network or attack files. Therefore, with the support of a specialized company like Bot, the chances of finding the malware and removing it without having to pay the ransom are significantly increased.
List of ransomware: which are the best known?
A Kaspersky Lab survey of users whose computers were targeted by crypto ransomware attacks in 2020 showed what the main variants were. The options with (*) are generic verdicts, where it was probably not confirmed exactly what the ransomware was.
- WannaCry / Trojan-Ramson.Win32.Wanna: 16.56%.
- Trojan-Ransom.Win32.Phny(*): 11.56%.
- Trojan-Ransom.Win32.Gen(*): 11.37%.
- Stop / Trojan-Ransom.Win32.Stop: 7.76%.
- Trojan-Ransom.Win32.Encoder(*): 6.66%.
- Trojan-Ransom.Win32.Generic(*): 4.77%.
- Trojan-Ransom.Win32.Crypren(*): 4.07%.
- PolyRansom/VirLock / Virus.Win32.PolyRansom: 2.54%.
- Crysys/Dharma / Trojan-Ransom.Win32.Crysis: 2.21
- Trojan-Ransom.Win32.Crypmod(*): 1.83%.
In addition to this data, we have separated a list of ransomware with some very common types. Check it out:
- Bad Rabbit: a variant that attacked companies in Russia and Eastern Europe, spread via a fake Adobe Flash update on compromised websites. When it infects a machine, victims are directed to make a payment of 0.05 Bitcoin.
- Cerber: focused on Microsoft 365 users, in the cloud, has already impacted millions of users with a well-crafted phishing campaign.
- CryptoLocker: one of the best known ransomwares, brought this type of malware into prominence. The botnet was shut down in May 2014, but the hackers managed to extort approximately $3 million from victims. CryptoLocker’s approach has been copied by other ransomware, although these are not directly linked to the original.
- CryptoWall: Gained notoriety after the fall of CryptoLocker. Distributed by spam or exploit kits, it appeared in early 2014 and has a wide variety of names, such as CryptoWall 2.0, CryptoWall 3.0, CryptoBit and CryptoDefense.
- Crysis: Encrypts files on fixed and removable disks, and on networks, with a very complicated algorithm. It is usually spread by e-mails with attachments, with double extension, that make it difficult to understand that they are executable files.
- CTB-Locker: In this ransomware, the strategy is different. Hackers make the infection process available to partners in exchange for a share of the profits. This is a strategy that allows you to achieve even higher volumes and thus faster infections.
- GoldenEye: similar to Petya, it is spread by large-scale campaigns that focus on Human Resource departments. As soon as the file is downloaded, a macro is launched that encrypts files on the computer. To each encrypted file GoldenEye adds a random 8-character extension. It also modifies the Master Boot Record (MBR) of the user’s hard disk by a custom boot loader.
- Jigsaw: Encrypts and progressively deletes files until the ransom is paid. A single file is deleted after the first hour, at a rate that increases every hour until it reaches 72 hours, when all remaining files are deleted.
- KeRanger: supposedly discovered in a popular BitTorrent client, it is not as widely distributed as other variants, but is known as the first fully functional ransomware designed to lock Mac OS X applications.
- LeChiffre: Unlike others, LeChiffre needs to be run manually on the compromised system. Criminals automatically scan networks for remote desktops with low security, logging in remotely and thereby manually executing an instance of the virus.
- LockerGoga: has already hit several European companies, such as Norsk Hydro, having infiltrated the company via a phishing email. This caused a global IT outage and forced the purchase of hundreds of new computers.
- Locky: the malware is spread by e-mail as an invoice, but when it is opened, it is scrambled. The victim is then instructed to allow macros to read the document, and when this happens Locky begins to encrypt large volumes of data with AES encryption.
- Maze ransomware: discovered in 2019, it has become known for releasing victims’ data, especially in the healthcare sector. Xerox also had more than 100 GB of data stolen by him.
- NotPetya: initially listed as a variant of Petya, researchers believe this to be malware known as a “wiper,” with the sole purpose of destroying data rather than obtaining a ransom.
- Petya: Unlike other ransomware, Petya encrypts entire computer systems by overwriting the MBR and preventing the system from booting.
- Ryuk: having achieved multiple victims, especially throughout 2020, it is used in attacks targeting businesses, hospitals, and municipalities. It encrypts critical files and demands very high, often million-dollar, payments.
- Spider: distributed by e-mail in Europe, is hidden in Word documents that install the malware on the computer when they are downloaded. The document has several malicious macros, and when executed, the ransomware starts downloading and encrypting the victims’ data.
- TeslaCrypt: also works with AES algorithms and is usually distributed by the Angler exploit kit, especially attacking Adobe vulnerabilities. When a vulnerability is exploited, TeslaCrypt installs itself in the Microsoft Temp folder.
- TorrentLocker: usually distributed by geographically focused email campaigns at strategic points. It uses the AES algorithm to encrypt files, and also collects email addresses from the victim’s contact list so that it can spread to the infected computer, a particularity of TorrentLocker.
- WannaCry: very well known, has affected over 125,000 companies in more than 150 countries. Affects Windows machines via a Microsoft exploit known as EternalBlue.
- ZCryptor: malware that propagates itself and exhibits “worm behavior” by encrypting files and infecting external storage drives in order to be distributed to other computers.
While these are among the most common, there are several other types of ransomware, with different characteristics and means of transmission, as well as new ransomware that is created over time.
What devices and systems can ransomware attack?
Windows, Linux, and MacOS computers, as well as Android and iOS devices. In practice, no one is totally immune to them.
A survey of more than 1,000 managed service providers, available on the Statista portal, asked which systems they have seen infected by ransomware, and they could choose more than one alternative. The answers were as follows:
- Windows: 91
- Windows Server: 76
- Windows Tablet: 8%.
- MacOS X: 7%.
- Android: 6%.
- iOS: 4%.
Windows tops the list by far, but other systems are also subject to being infected by ransomware.
How do I know if my device is infected by ransomware?
There is no definitive way to tell if your device is infected by ransomware, as each one acts in its own way, but some signs should be considered, such as the following:
- Locked browser or desktop, with a message about how to pay to unlock the system;
- Folders containing a “ransom note”, usually in .txt files;
- All files get a new extension after their original names, such as .exx, .zzz, .xxx, .micro, .encrypted, .crypto, .locked, .LOL!, .RDM, .magic, .SUPERCRYPT and the like;
- Repeated suspicious activity, usually at the same time of day, as if it were the action of a virus.
If you notice any of these signs, contact Bot as soon as possible for a thorough analysis of the device. The sooner a potential ransomware attack is identified, the better.
What can I do to protect myself against a ransomware attack?
Prevention is one of the best ways to avoid a ransomware attack, and the following tips can help you in this regard:
- Make constant backups. If you are a victim of ransomware, but have your data safe, then you have no reason to worry. Ideally, you should opt for cloud storage or external drivers.
- Be careful with suspicious e-mails and messages. If you notice anything strange, contact the person who supposedly sent that e-mail. If the sender is unknown, double your attention.
- Do not download attachments whose origin you do not know. Whether it is a spreadsheet, a text document, or a PDF, if you are not sure of its origin, the best thing to do is to avoid opening it, as it could be a trap.
- Keep your programs and operating system up to date. Updates often bring additional security measures, which is always important to avoid breaches.
- Develop a disaster recovery plan. Having a Disaster Recovery Plan (DRP) is critical, especially for enterprises. The plan may include several steps, such as turning off most of the network, Wi-Fi and Bluetooth of the devices, and even alerting the authorities.
They Encrypted My Files: Now What?
If you have been the victim of a ransomware attack, it is best to seek professional help to avoid further problems. We know that this type of infection causes huge headaches, but having professionals to take care of it helps a lot.
In general, victims have three options when they detect ransomware on their device:
- Pay the ransom and hope that the criminals return the tool with the solution (which does not happen in 30% of cases);
- Look for a company that specializes in encrypted data recovery that is recognized and has proven results (such as Bot);
- Restore your computer to factory settings and lose all data.
In any case, it is important not to give in to the blackmail of criminals. It is recommended not to pay the ransom, since the amounts are high, the payment is complex, there is no certainty that you will get your data back, and the payment even encourages this type of crime.
Moreover, the other options demand experience and knowledge, as well as specialized tools. Therefore, it is important to seek professional help as soon as possible. If it is possible to scan the file structure affected by the ransomware without much modification, the chances of recovery are greater.
How to decrypt a file?
If you believe you have been the victim of a ransomware attack and want to know how to recover virus-encrypted files, the best thing to do is to contact Bot immediately, as incorrect procedures can make recovery difficult.
This is a very technical procedure. It requires a thorough analysis of each case, which should be done by specialists with enough experience in recovering encrypted files.
Remove Encryption Ransomware
After doing an analysis of the infection, removing the encryption in a ransomware attack should be done with a decryption tool or using professional file editing processes.
There are different tools for different types of ransomware, so it is important to have professionals who know how to identify them and adopt the appropriate platform.
How does the recovery of encrypted files work?
Initially, our technicians analyze the situation to determine the safest and most cost-effective option for recovering the encrypted files.
All possibilities are evaluated in a specific study about the type of ransomware, how it works, and the security holes it has. With this we will know if the process can be reversed to decrypt the data.
If this is not possible, we have a team of specialists who can do an in-depth analysis of the file structure. The intention is to check the traces left during the infection in order to reconstruct as many files as possible.
All possible procedures will be performed to increase the chances of recovering your encrypted files in the most efficient and secure way.
It is very important that you reach out to Bot as soon as possible, as some ransomware can delete the files after some time. Besides the free estimate (48 hours), we also have the priority (24 hours) or urgency (12 hours) options, which speed up the procedures even more.
Our team works 24 hours a day, 7 days a week, 365 days a year. This means that you will have all the support you need to get out of this situation.
99% of Bot’s customers are satisfied with the result, and the average rating received from our customers on social networks is 4.9/5.0. In addition, we have a 95% success rate in the cases received, which proves the quality of the services provided.
Don’t waste any more time and get rid of data hijacking by ransomware attack quickly, with all the security and efficiency you deserve!


